This post is the fourth of a series on Threat Intelligence Automation topic.
Post 1: Architecture and Hardening of MineMeld
Post 2: Foundation: write a custom prototype and SOC integration
Post 3: Export internal IoC to the community
Post 5: Connect to a TAXII service
After having laid the foundations for building a community with the previous posts, it’s now time to make some advanced analysis of the received IoC.
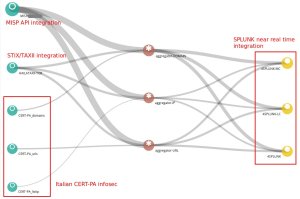
In post 2 I integrated MineMeld output nodes into Splunk SOC near-real-time engine to automate SOC IoC access detection. This configuration strengthens the analysis and response capabilities of our SOC.
With this post I show you how to integrate MineMeld miners IoC events (update and withdraw of remote IoC) into Splunk engine so you can use Splunk search advanced features to have a deeper look into the IoC received from the miners.
This is also an important information for a SOC because if you have an IoC hit the first think to do is to understand where the IoC come from, if it was sent by more than one source etc